作为网络设备,其安全的重要性不言而喻。如何确保这些设备及所连接网络的安全成为很多网络管理及专业从事网络安全人员的重要责任及义务之一,下面就几种常用的安全配置方法做一简要说明,希望能有抛砖引玉之效!
Recommended Switch Security
☆Set system secret
☆Configure basic ACLs
☆Secure physical access to the console
☆Secure access to VTYs
☆Configure system warning banners
☆Disable unneeded services
☆SSH
☆Trim CDP
☆Disable the integrated HTTP daemon
☆Configure basic logging
☆Secure SNMP
☆Limit trunking connections
☆Secure the spanning-tree topology
几个常用安全配置
Switch # no service finger
Switch # no service tcp-small-servers
Switch # ssh secure shell //ssh通过加密传输,较telnet安全
Switch # snmp v3/v2c //snmp v3/v2c采用加密技术,v1使用明文传输
AAA Network含义
Authentication (认证) – Verifies a user’s identify
Authorization (授权) – Specifies the permitted tasks for the user
Accounting (记账) – Provides billing , auditing , and monitoring
Configure AAA Network
Configure Authentication(配置认证)
Switch(config) # aaa new-model
Switch(config) # aaa authentication login { default | list-name } method1 [ method2 … ]
//配置aaa登陆认证方法
Switch(config) # line [ aux | console | tty | vty ] line-number [ ending-line-number ]
//进入端口配置模式
Switch(config-line) # login authentication { default | list-name }
例:
Switch(config)# aaa new-model
Switch(config)# aaa authentication login myway tacacst+ radius local
//交换机将用户输入的用户名、密码等信息发送到tacacst+或radius服务器上,local是本地认证的意思
Switch(config)# line vty 0 4
Switch(config-line)#login authentication myway
Configure Authorization(配置授权)
Switch(config)# aaa authorization { auth-proxy | network | exec | commands level | reverse-access | configuration | ipmobile } { default | list-name } [ method1 [ method2 … ] ]
Switch(config)# interface interface-type interface-number
Switch(config-if)#ppp authorization { default | list-name }
Configure Accounting(配置记账)
Switch(config)# aaa accounting { system | network | exec |connection | commands level } { default | list-name } { start-stop | stop-only | none } [ method1 [ method2… ] ]
Switch(config)# interface interface-type interface-number
Switch(config-if)# ppp accounting { default | list-name }
端口安全性的配置
Switch(config)#switchport port-security [ maximum value] violation { protect | restrict | shutdown }
Configure 802.1X port-based Authentication
Switch (config)#aaa authentication dot1x { default } method1 [ method2… ]
Switch (config)#dot1x system-auto-control //激活802.1x
Switch (config)#interface type slot/port
Switch (config-if)#dot1x port-control { force-authorized | force-unauthorized | auto }
例:
Switch (config)#aaa new-model
Switch (config)#aaa authentication dot1x default group radius
Switch (config)#dot1x system-auto-control
Switch (config)#int fa 5/6
Switch (config-if)#dot1x port-contro auto
检验端口安全性配置
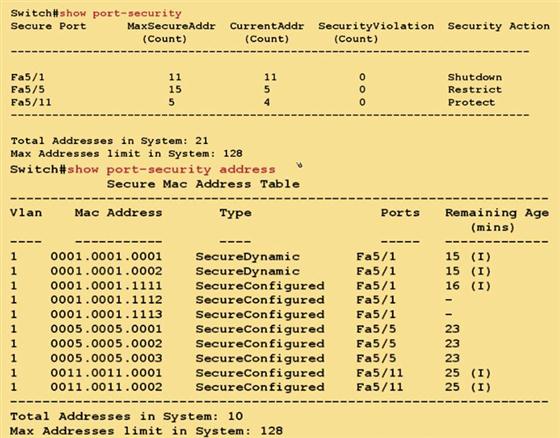
Switch # show port-security
Switch # show port-security [interface type slot/port ]
Switch # show port-security address
ACL访问控制列表
Type of ACLs : RACL(Router ACL)、QOS ACL、VLAN ACL
Configure VACLs
Switch (config) # vlan access-map map_name [seq#]
Switch (config-access-map) # match { ip address { 1-99 | 1300-2699 | acl_name} | ipx address { 800-999 | acl_name } | mac address acl_name }
Switch (config-access-map) # action { drop [log]}| {forward [capture]} | {redirect { type slot/port} | {port-channel channel_id}}
Switch (config)#vlan filter map_name vlan_list list
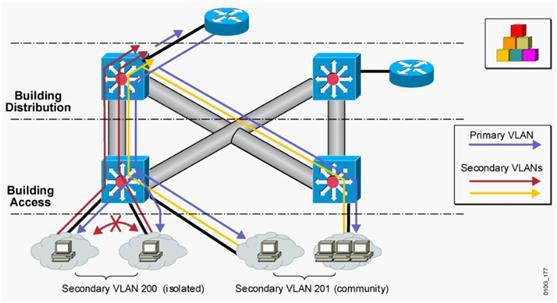
Private VLAN
PVLAN解决了禁止相同vlan间不同端口的相互访问(宾馆、小区内有此类需求)。
PVLAN Ports and Types
Private VLAN ports:
Promiscuous(混杂端口) : Can communicate with all other ports;
Isolated(隔离端口) : Can only communicate with promiscuous ports;
Community(团体端口) :Can communicate with other members of community and all promiscuous ports
Private VLAN types:
Primary(主VLAN) :Used by promiscuous ports to communicate with all other ports in the private VLAN.
Isolated(隔离VLAN) :Used by Isolated ports to communicate with Promiscuous ports. (每个PVLAN中只能有一个isolated VLAN)
Community(团体VLAN) :Used by community ports to communicate with each other and promiscuous ports. (每个PVLAN可以有多个community VLAN)
Configure private VLAN
Switch(config-vlan)# private-vlan [ primary | isolated | community ]
将该VLAN定义为一个私有VLAN,并指定其私有VLAN类型
Switch(config-vlan)# private-vlan association { secondary_vlan_list | add svl |remove svl }
关联、添加、删除主从VLAN
Switch#show vlan private-vlan type
Configure private VLAN ports
Switch(config-if)# switchport mode private-vlan { host | promiscuous }
Configure an interface as a private VLAN port.其中host为将端口设置成为隔离/团体端口模式,promiscuous为混杂模式端口。
Switch(config-if)# switchport private-vlan host-association primary_vlan_ID secondary_vlan_ID
Associates an isolated or community port with a privateVLAN.关联隔离端口及团体端口和私有VLAN的对应关系。
Switch(config-if)#private-VLAN mapping primary_vlan_ID { secondary_vlan_ID | add svl | remove svl }
Maps a promiscuous pvlan port to a private VLAN.关联混杂模式端口和PVLAN的对应关系。
Switch#show interfaces private-vlan mapping
例1:#
Switch(config)#vtp mode transparent
Switch(config)#vlan 202
Switch(config-vlan)#private-vlan primary
Switch(config-vlan)#private-vlan association 440
Switch(config)#vlan 440
Switch(config-vlan)#private-vlan islated
Switch(config)#int fa5/2
Switch(config-if)#switchport mode private-vlan promiscuous
Switch(config-if)#switchport private-vlan mapping 202 440
Switch(config)#int fa5/1
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 202 440
Switch(config)#int vlan 202
Switch(config-vlan)#private-vlan mapping add 440 //将vlan440流量可路由到vlan202
例2:#
Switch(config)#vlan 10
Switch(config-vlan)#private-vlan primary //建立primary VLAN
Switch(config)#vlan 11
Switch(config-vlan)#private-vlan isolated //建立isolated VLAN
Switch(config)#vlan 12
Switch(config-vlan)#private-vlan community //建立community VLAN
Switch(config)#vlan 10
Switch(config-vlan)#private-vlan association 11,12 //关联primary VLAN与Second VLANs
Switch(config)#interface G0/0
Switch(config-if)#switchport
Switch(config-if)#switchport mode private-vlan promiscuous
Switch(config-if)#switchport private-vlan mapping 10 11,12 //配置promiscuous
注:
这里promiscuous port可以属于多个secondary VLAN,但只可以属于一个primary VLAN,就好像普通的access port只能属于一个vlan是一样的。
Switch(config)#interface G0/1
Switch(config-if)#switchport
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 10 11 //配置isolated port
Switch(config)#interface G0/2
Switch(config-if)#switchport
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 10 12 //配置community port
注意:
1>在private vlan里 switchport access vlan xxx 这一句已经不起作用了。
起作用的是 switchport private-vlan host-association 10 11这一句,这一句把端口放入primary vlan 10和secondary vlan 11。
2>在配置vlan的3层地址的时候,只可以配置在primary VLAN上,从这里也可以看出,primary VLAN在某些地方是和普通vlan一样工作的,secondary VLAN则更特殊一些。
总结起来,其实也不外乎AAA认证以及vlan等知识的巧妙使用(当然还有很多其他方法,在此不再一一赘述),具体使用方法呢,还是需要读者在使用这些功能慢慢体会!
