ACL访问控制列表的配置
接前面几篇文章所述,想到了一个概念:PVLAN。私有vlan的应用也是非常广泛的,可以显著提升您的网络安全及网络性能,下面就介绍一下cisco在这个方面的配置:
ACL访问控制列表
Type of ACLs : RACL(Router ACL)、QOS ACL、VLAN ACL
Configure VACLs
Switch (config) # vlan access-map map_name [seq#]
Switch (config-access-map) # match { ip address { 1-99 | 1300-2699 | acl_name} | ipx address { 800-999 | acl_name } | mac address acl_name }
Switch (config-access-map) # action { drop [log]}| {forward [capture]} | {redirect { type slot/port} | {port-channel channel_id}}
Switch (config)#vlan filter map_name vlan_list list
Private VLAN
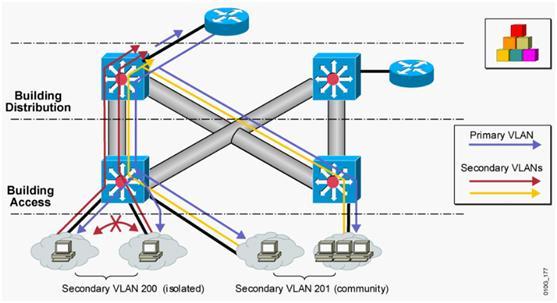
PVLAN解决了禁止相同vlan间不同端口的相互访问(宾馆、小区内有此类需求)。
PVLAN Ports and Types
Private VLAN ports:
Promiscuous(混杂端口) : Can communicate with all other ports;
Isolated(隔离端口) : Can only communicate with promiscuous ports;
Community(团体端口) :Can communicate with other members of community and all promiscuous ports
Private VLAN types:
Primary(主VLAN) :Used by promiscuous ports to communicate with all other ports in the private VLAN.
Isolated(隔离VLAN) :Used by Isolated ports to communicate with Promiscuous ports. (每个PVLAN中只能有一个isolated VLAN)
Community(团体VLAN) :Used by community ports to communicate with each other and promiscuous ports. (每个PVLAN可以有多个community VLAN)
Configure private VLAN
Switch(config-vlan)# private-vlan [ primary | isolated | community ]
将该VLAN定义为一个私有VLAN,并指定其私有VLAN类型
Switch(config-vlan)# private-vlan association { secondary_vlan_list | add svl |remove svl }
关联、添加、删除主从VLAN
Switch#show vlan private-vlan type
Configure private VLAN ports
Switch(config-if)# switchport mode private-vlan { host | promiscuous }
Configure an interface as a private VLAN port.其中host为将端口设置成为隔离/团体端口模式,promiscuous为混杂模式端口。
Switch(config-if)# switchport private-vlan host-association primary_vlan_ID secondary_vlan_ID
Associates an isolated or community port with a privateVLAN.关联隔离端口及团体端口和私有VLAN的对应关系。
Switch(config-if)#private-VLAN mapping primary_vlan_ID { secondary_vlan_ID | add svl | remove svl }
Maps a promiscuous pvlan port to a private VLAN.关联混杂模式端口和PVLAN的对应关系。
Switch#show interfaces private-vlan mapping
例1:#
Switch(config)#vtp mode transparent
Switch(config)#vlan 202
Switch(config-vlan)#private-vlan primary
Switch(config-vlan)#private-vlan association 440
Switch(config)#vlan 440
Switch(config-vlan)#private-vlan islated
Switch(config)#int fa5/2
Switch(config-if)#switchport mode private-vlan promiscuous
Switch(config-if)#switchport private-vlan mapping 202 440
Switch(config)#int fa5/1
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 202 440
Switch(config)#int vlan 202
Switch(config-vlan)#private-vlan mapping add 440 //将vlan440流量可路由到vlan202
例2:#
Switch(config)#vlan 10
Switch(config-vlan)#private-vlan primary //建立primary VLAN
Switch(config)#vlan 11
Switch(config-vlan)#private-vlan isolated //建立isolated VLAN
Switch(config)#vlan 12
Switch(config-vlan)#private-vlan community //建立community VLAN
Switch(config)#vlan 10
Switch(config-vlan)#private-vlan association 11,12 //关联primary VLAN与Second VLANs
Switch(config)#interface G0/0
Switch(config-if)#switchport
Switch(config-if)#switchport mode private-vlan promiscuous
Switch(config-if)#switchport private-vlan mapping 10 11,12 //配置promiscuous
注:
这里promiscuous port可以属于多个secondary VLAN,但只可以属于一个primary VLAN,就好像普通的access port只能属于一个vlan是一样的。
Switch(config)#interface G0/1
Switch(config-if)#switchport
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 10 11 //配置isolated port
Switch(config)#interface G0/2
Switch(config-if)#switchport
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 10 12 //配置community port
注意:
1>在private vlan里 switchport access vlan xxx 这一句已经不起作用了。
起作用的是 switchport private-vlan host-association 10 11这一句,这一句把端口放入primary vlan 10和secondary vlan 11。
访问控制列表及地址转换配置实验http://www.chinavalue.net/Biz/Blog/2012-3-29/891121.aspx
